Use hostnamectl
https://www.cyberciti.biz/faq/how-to-change-hostname-on-debian-10-linux/
This is my tech junk… Pretty much a catch all.
Use hostnamectl
https://www.cyberciti.biz/faq/how-to-change-hostname-on-debian-10-linux/
firewall {
all-ping enable
broadcast-ping disable
ipv6-receive-redirects disable
ipv6-src-route disable
ip-src-route disable
log-martians enable
name WAN_IN {
default-action drop
description "WAN to Internal"
enable-default-log
rule 1 {
action accept
description "Allow established/related"
log disable
state {
established enable
related enable
}
}
rule 2 {
action drop
description "Drop invalid state"
log enable
state {
invalid enable
}
}
}
name WAN_LOCAL {
default-action drop
description "WAN to Router"
enable-default-log
rule 1 {
action accept
description "Allow established/related"
log disable
state {
established enable
related enable
}
}
rule 2 {
action drop
description "Drop invalid state"
log enable
state {
invalid enable
}
}
}
options {
mss-clamp {
interface-type all
mss 1460
}
}
receive-redirects disable
send-redirects enable
source-validation disable
syn-cookies enable
}
interfaces {
ethernet eth0 {
address 192.168.0.1/24
description "Local Config Port"
duplex auto
poe {
output off
}
speed auto
}
ethernet eth1 {
description "Google Fiber Jack"
duplex auto
poe {
output 48v
}
speed auto
vif 2 {
address dhcp
address dhcpv6
description "Google Fiber WAN"
egress-qos 0:3
firewall {
in {
name WAN_IN
}
local {
name WAN_LOCAL
}
}
}
}
ethernet eth2 {
description "LAN 0"
duplex auto
poe {
output off
}
speed auto
}
ethernet eth3 {
description "LAN 1"
duplex auto
poe {
output off
}
speed auto
}
ethernet eth4 {
description "LAN 2"
duplex auto
poe {
output off
}
speed auto
}
loopback lo {
}
switch switch0 {
address 10.1.0.1/24
description "LAN Switch"
mtu 1500
switch-port {
interface eth2
interface eth3
interface eth4
}
}
}
port-forward {
auto-firewall enable
hairpin-nat enable
lan-interface switch0
wan-interface eth1.2
}
service {
dhcp-server {
disabled false
hostfile-update enable
shared-network-name LAN {
authoritative disable
subnet 10.1.0.0/24 {
default-router 10.1.0.1
dns-server 10.1.0.1
lease 86400
start 10.1.0.101 {
stop 10.1.0.254
}
}
}
}
dns {
forwarding {
cache-size 1000
listen-on switch0
name-server 2001:4860:4860::8888
name-server 2001:4860:4860::8844
name-server 8.8.8.8
name-server 8.8.4.4
}
}
gui {
https-port 443
}
nat {
rule 5000 {
description "Masquerade for WAN"
log disable
outbound-interface eth1.2
protocol all
type masquerade
}
}
ssh {
port 22
protocol-version v2
}
upnp2 {
listen-on switch0
nat-pmp disable
secure-mode disable
wan eth1.2
}
}
system {
host-name edgy-loop
login {
user ubnt {
authentication {
encrypted-password $1$zKNoUbAo$gomzUbYvgyUMcD436Wo66.
plaintext-password ""
}
level admin
}
}
name-server 2001:4860:4860::8888
name-server 2001:4860:4860::8844
name-server 8.8.8.8
name-server 8.8.4.4
ntp {
server 0.ubnt.pool.ntp.org {
}
server 1.ubnt.pool.ntp.org {
}
server 2.ubnt.pool.ntp.org {
}
server 3.ubnt.pool.ntp.org {
}
}
offload {
ipsec enable
ipv4 {
forwarding enable
vlan enable
}
ipv6 {
forwarding disable
}
}
syslog {
global {
facility all {
level notice
}
facility protocols {
level debug
}
}
}
time-zone America/Chicago
}
Two Factor Authentication is a lofty goal for any linux administrator. If you’re lucky enough to have access to an NetIQ eDirectory server, hardware based two factor authentication is closer than you think.
Tutorial on how to use SSSD (pronounced Triple “S” D) as a cross Linux platform (RHEL, SLES, Ubuntu, et. al) authentication agent instead of painful and often times disparate pam_ldap and sudoers configurations. Centralized user and group management using existing directory infrastructure. Learn how centrally store SSH key and sudoer configurations in LDAP. No more having to copy your SSH key to each new server. Create a SSH Key based single sign on solution. Your sudo commands are authenticated against your Directory. Expand the configuration of SSSD clients for 2 factor authentication using a HOTP configured YubiKey that does not require any changes on the authenticating client. Integration with eDirectory. Explore SSO Kerberized options with Active Directory and MIT Kerberos.
Requirements:
/usr/java/jre1.7.0/bin/keytool -importcert -trustcacerts -noprompt \ -alias custom-root-ca \ -storepass changeit \ -file /etc/ssl/certs/CERT.pem \ -keystore /usr/java/jre1.7.0/lib/security/cacerts
Install Windows 7 using default settings. We will customize this install. I’m using a virtual machine running in VMware Fusion so I can snapshot the progress.
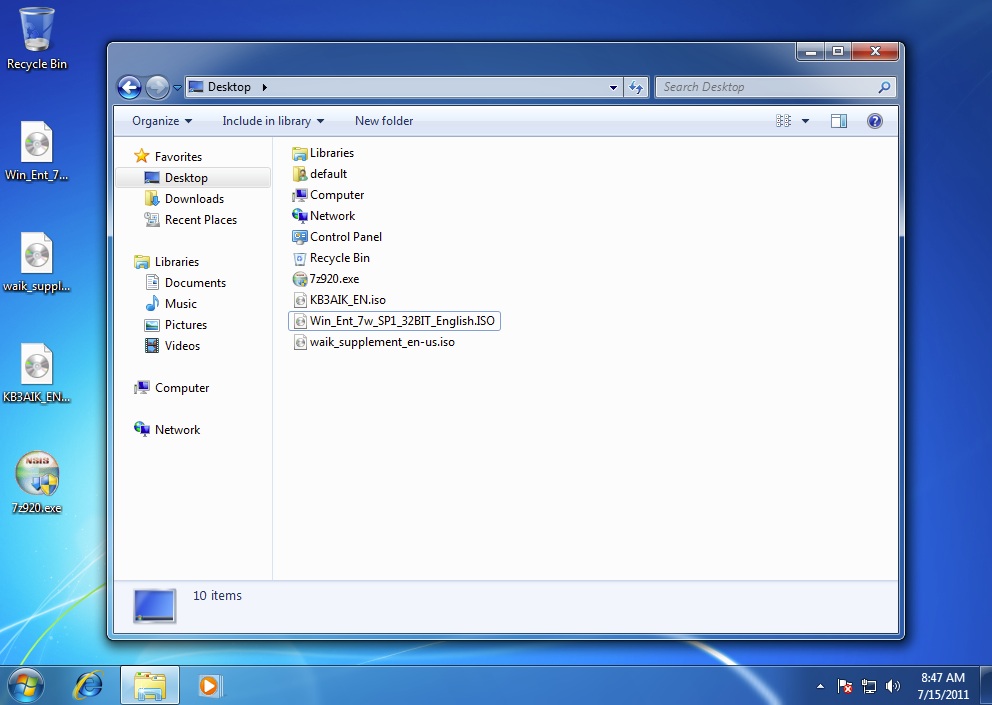
Extract the contents of the isos to the desktop using: Right click -> 7zip –> Extract to “foldername”. You should now have three folders on your desktop with the contents of the three isos.
From the KB3AIK_EN folder run the wAIKX86.msi (wAIKAMD64.msi if you’re installing a 64bit windows)
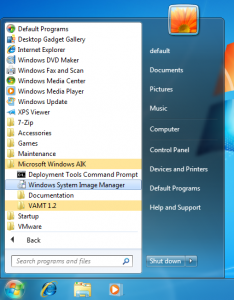
This will walk through loading a windows image (in this case the image is the install DVD) into the System Image Manager.
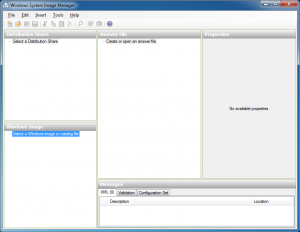
In the bottom left pane titled Windows Image, right click and select “New Image”.
Brows to the location where you extracted windows 7 iso (Desktop), and brows to the sources folder and choose the cataloge file (.clg extension) “install_Windows 7 Enterprise.clg”.
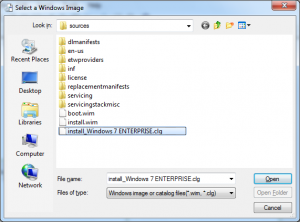
Now we have the Windows image Loaded into the image manager. The next step will walk through creating an answer file.
Step 5 – Creating the answer file
— TODO — Create the File
Step 6 – Running Sysprep
In another VM instance start a vanilla 7 installation. When you arrive at the welcome screen where it asks you to create a username, hit CTRL+SHIFT+F3, this will reboot your machine and put you in “audit” mode.
PKCS #12 is one of the family of standards called Public-Key Cryptography Standards (PKCS), published by RSA Laboratories. It defines a file format commonly used to store X.509 private keys with accompanying public key certificates, protected with a password-based symmetric key PFX Certificate?
In practice .pfx is just another file extension for a PKCS#12 or .p12 type certificate.
This command will convert a pfx certificate to a X509 pem encoded certificate. The use of the -nodes flag will give the option to password protect the private key in the new pem encoded certificate. For information on converting pem to der encoded certificates.
openssl pkcs12 -in Certificate.pfx -out NewCertificate.pem
openssl pkcs12 -in Certificate.pfx -out NewCertificate.pem -nodes
openssl pkcs12 -in Certificate.pfx -out NewCertificate.pem -nokeys -clcerts
openssl pkcs12 -in certificate.pfx -out certificate.key -nocerts -nodes
openssl pkcs12 -in certificate.pfx -out ca-chain.pem -nokeys -cacerts
If you do have Keytool application and your PKCS#12 file, launch the one-line command:
keytool -importkeystore -srckeystore source.p12 -srcstoretype pkcs12
-srcalias Alias -destkeystore target.jks -deststoretype jks
-deststorepass password -destalias Alias
To extract or “unbuild” and RPM so you can see its files you have to use two programs. The first is rpm2cpio, the second is cpio.
rpm2cpio: Extract cpio archive from RPM Package Manager (RPM) package.
cpio – allows a user to copy file to and from an archive.
[code lang=”bash” title=”Do this as root”]linux:/tmp/rpmsource# rpm2cpio <>.src.rpm | cpio -idmv [/code]
Explanation: rpm2cpio takes the rpm and runs the extraction that is then piped through cpio to extract the files to a local directory. FLAGS: -i extract, -d make directories where needed, -m preserve modification time, -v verbose mode will list the names of the files as they are extracted.
I’m not sure if this will work for non-src rpms.
** This post is pretty incomplete, I gave up on it. But there is enough info here that may be usefull**
eDirectory has several attributes for photos, here are the raw schema attributes from an eDirectory install from iMonitor. An interesting note is that ldapPhoto and photo have the same OID. Because the syntax is Octet String I think that the photos can be stored as either Binary Data or as a Base64 encoded representation of the image.
| Attribute Name |
Flags
|
Syntax
|
Lower Limit
|
Upper Limit
|
OID
|
Used By Class
|
|---|---|---|---|---|---|---|
| jpegPhoto | Sync. Immediate | Octet String | 0 | 4294967295 | 0.9.2342.19200300.100.1.60 | User |
| ldapPhoto | Sync. Immediate | Octet String | 0 | 4294967295 | 0.9.2342.19200300.100.1.7 | User |
| photo | Sync. Immediate | Octet String | 0 | 4294967295 | 0.9.2342.19200300.100.1.7 | Person |
Using and populating these attributes can be tricky. If you use Identity Manager, the User Application stores pictures in the photo attribute.
rfc2798 defines
2.6. JPEG Photograph
Used to store one or more images of a person using the JPEG File
Interchange Format [JFIF].
( 0.9.2342.19200300.100.1.60
NAME 'jpegPhoto'
DESC 'a JPEG image'
SYNTAX 1.3.6.1.4.1.1466.115.121.1.28 )
Note that the jpegPhoto attribute type was defined for use in the
Internet X.500 pilots but no referencable definition for it could be
located.